The Windows Registry is a central storage for settings in Windows, and also a popular target of hacks to enable/disable obscure features. But how does it work? Where does it store all the data? What options are available in it? In this post I plan to go through the internals of the registry.
Overview
The registry is a hierarchical key-value storage system, that keeps its elements in a tree-like structure, much like a file system. The values have data types so not only strings but integers and binary data can be stored as well.
The “folders” in the registry are called keys. This is unlike other key-value stores, like Redis, where key refers to the id of a value. The actual key-value pairs inside these folders are called name-data pairs. For example, HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion is a key, and the name ProgramFilesDir under this key holds the path to the “Program Files” folder. This strange naming has historical reasons: in the original version of the registry (in Windows 3.1) keys could store only a single value. This naming scheme was kept for backward-compatibility. It is also the reason why each key has a ‘default’ value.
Data types
One advantage of the registry over simple ini files is that it can store typed data, and possibly binary data. Some of the more important datatypes:
| ID | Symbolic Name | Description |
|---|---|---|
| 0 | REG_NONE | No type |
| 1 | REG_SZ | A string |
| 2 | REG_EXPAND_SZ | An expandable string: can contain environment variables that are substituted |
| 3 | REG_BINRAY | Binary data |
| 4 | REG_DWORD | A 32 bit integer (double word) |
| 6 | REG_LINK | Symbolic link to another registry key |
| 7 | REG_MULTI_SZ | An array of strings, strings are separated by the NUL character |
| 11 | REG_QWORD | A 64-bit integer (quad word) |
There are other types available, the full list is available here.
Hives
The registry is not stored as a single file on disk but as multiple files, each representing one subtree of the full registry. For example, HKEY_CURRENT_USER is stored in %user_home%\ntuser.dat. These files are called hives. However, hives and root keys do not have a one-to-one correspondence. Check the next section on how each root key is actually stored.
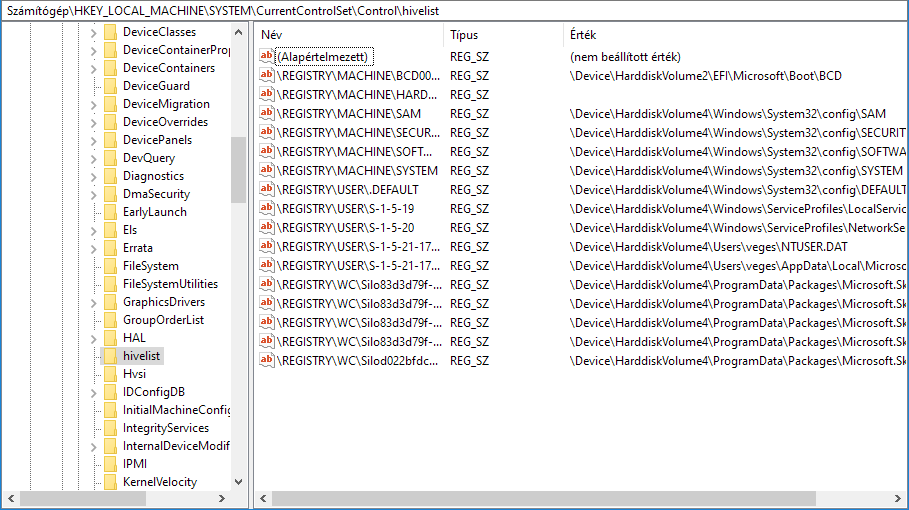
You can list the available hives in the registry itself: they are stored under HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\hivelist. It lists all the hives with the locations they are mounted at.
The hive files use a binary dataformat. The basic element in the file is the cell. A cell can be a key, a value (with name and data), a list of keys or a list of values. Then a key cell points to a list-of-keys cell to represent its subkeys and to a list-of-values cell to represent the values under the key.
Windows also keep transaction logs for each hive. They have the same name as the hive, with an additional .log1 or .log2 suffix. These files ensure that if the computer crashes while the registry is edited, no data is lost. Why are there two log files? If the system stops while .log1 is written, the new data will be added to .log2. This serves as a double protection mechanism against crashes.
Root keys
Root keys are the top level keys in the database, their name all start with HKEY. In general, HKEY_LOCAL_MACHINE keeps the computer level settings, while HKEY_CURRENT_USER has the settings for the current user. When a program wants to access a certain setting it should first look into HKEY_CURRENT_USER then search HKEY_LOCAL_MACHINE for the key.
HKEY_LOCAL_MACHINE
This key stores the computer level settings that are not specific to any users. The SAM, SECURITY, SOFTWARE and SYSTEM subkeys are stored in the folder %windir%\system32\config, each in a different file. The HARDWARE key is not stored on disk: it is generated during startup and kept entirely in memory. The BCD00000000 key is a virtual mapping of the BCD database (Boot Configuration Data, where the bootloader keeps the information on the available operating systems).
The applications should place their settings in the SOFTWARE subkey, under a key named Vendor\ApplicationName.
HKEY_USERS
The user specific settings. Users are referred by the Security Identifiers (SID), it is a long string looking something like S-15-20-…. Usually only the current user is loaded, plus some additional virtual users used for LAN file sharing and SharePoint. Each user has two subkeys: one that is named after the SID of the user, and another that has _CLASSES appended to it. The latter contains information about registered applications, file types and OLE class IDs. The other contains all the additional user-level settings. Similarly to HKEY_LOCAL_MACHINE, programs should store their settings in Software\Vendor\ApplicationName. The keys are stored in the %user_home%\ntuser.dat and %user_home%\AppData\Local\Microsoft\Windows\usrclass.dat hives.
HKEY_CURRENT_USER
This is simply a pointer to the current user’s key in HKEY_USERS.
HKEY_CLASSES_ROOT
This key contains all information about file associations and registered COM components. While it is not stored directly on disk, it is neither a simple pointer to another key. Instead it merges the user level component information stored in HKEY_USER\current_user_sid_CLASSES and the system level information in HKLM\Software\Classes. If a key occurs in both places, the user-level value takes precedence.
HKEY_CURRENT_CONFIG
Contains information used by Windows during startup. It is a Pointer to HKEY_LOCAL_MACHINE\System\CurrentControlSet\Hardware Profiles\Current.